Webshag包装说明
Webshag是一个多线程,多平台Web服务器审计工具。用Python编写的,它收集像网站的抓取,URL扫描或文件模糊测试Web服务器的审计中很常用的功能。
Webshag可以用来扫描在HTTP或HTTPS web服务器,通过代理,并使用HTTP认证(基本和摘要)。此外,它提出了创新的IDS躲避功能旨在使要求更复杂的相关性(例如,使用每个请求的HTTP代理服务器不同的随机)。
资料来源:http://www.scrt.ch/en/attack/downloads/webshag
Webshag首页 | 卡利Webshag回购
- 作者:〜伤心〜,SCRT - 信息安全
- 许可:GPLv3的
包含在webshag包工具
webshag-CLI - 多线程Web服务器审计工具(CLI)
[email protected]:~# webshag-cli -h
Usage: webshag-cli [-U | [options] target(s)]
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-U Update the URL scanner databases and exit
-m MODULE Use MODULE [pscan|info|spider|uscan|fuzz]. (default: uscan)
-p PORT Set target port to PORT. For modules uscan and fuzz PORT can
be a list of ports [port1,port2,...]. (default: 80)
-r ROOT Set root directory to ROOT. For modules uscan and fuzz ROOT
can be a list of directories [/root1/,/root2/,...].
(default: /)
-k SKIP *uscan only* Set a false positive detection string
-s SERVER *uscan only* Bypass server detection and force server as
SERVER
-i SPIDER_INIT *spider) only* Set spider initial crawling page (default: /)
-n FUZZ_MODE *fuzz only* Choose the fuzzing mode [list|gen]. (default:
list)
-e FUZZ_CFG *fuzz / list only* Set the fuzzing parameters for list mode.
11 = fuzz directories and files; 01 = fuzz files only; 10 =
fuzz directories only; 00 = fuzz nothing. (default: 11)
-g FUZZ_GEN *fuzz / gen only* Set the filename generator expression.
Refer to documentation for syntax reference. (default: )
-x Export a report summarizing results.
-o OUTPUT Set the format of the exported report. [xml|html|txt].
(default: html)
-f OUTPUT_FILE Write report to FILE. (default: webshag_report.html)webshag贵 - 多线程Web服务器审计工具(GUI)
一个多线程,多平台的Web服务器审计工具。图形用户界面版本。
webshag-CLI用法示例
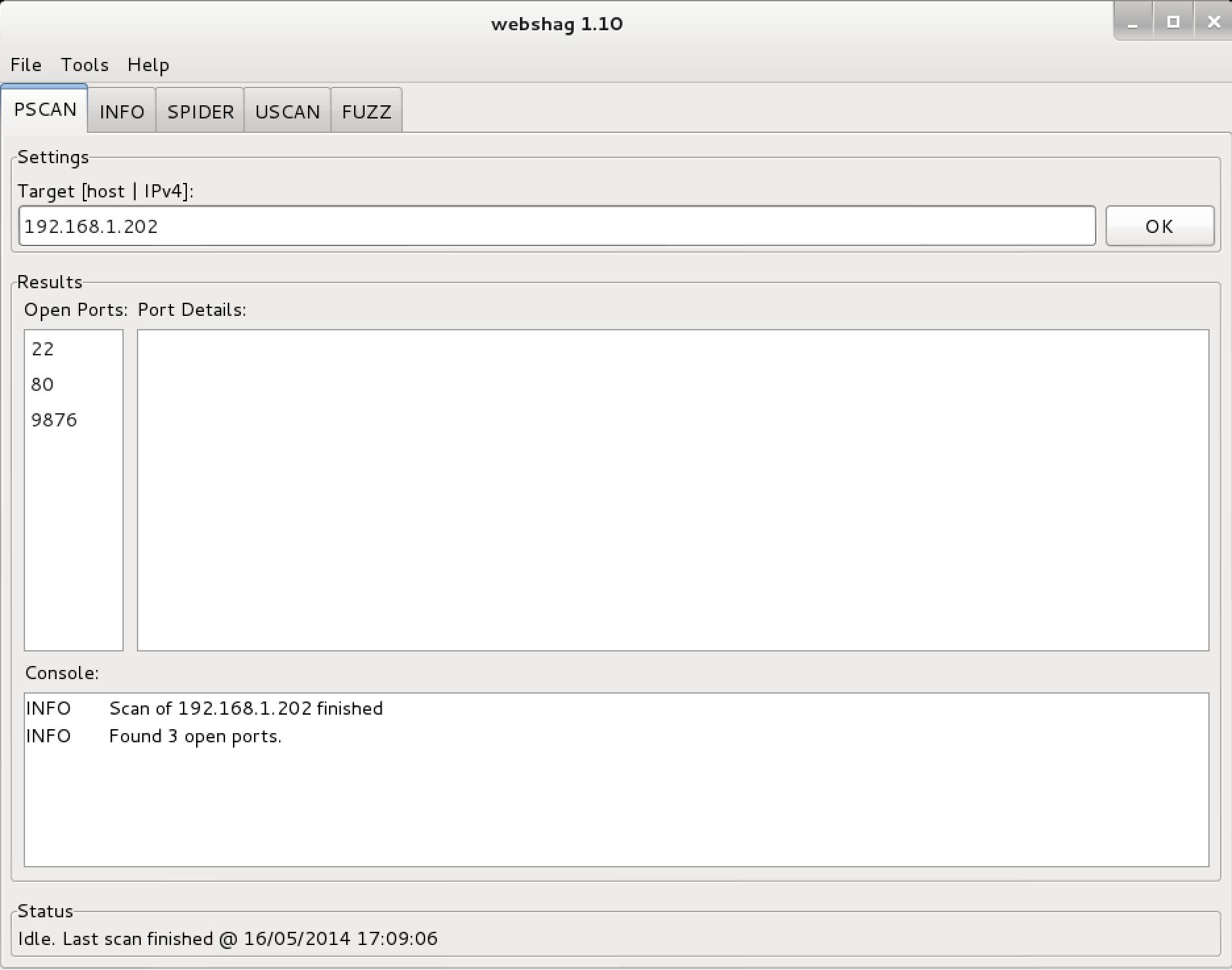
运行在远程IP地址(192.168.1.202)端口扫描(-m PSCAN):
[email protected]:~# webshag-cli -m pscan 192.168.1.202
~~~~~~~~~~~~~~~~~~~~~~~~~~ ## ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
% webshag 1.10
% Module: pscan
% Host: 192.168.1.202
~~~~~~~~~~~~~~~~~~~~~~~~~~ ## ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
192.168.1.202
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
% PORT % 22 (tcp)
% SRVC % ssh
% PROD % OpenSSH
% SYST % Linux
% PORT % 80 (tcp)
% SRVC % http
% PROD % Apache httpd
% PORT % 9876 (tcp)
% SRVC % http
% PROD % Apache httpd
~~~~~~~~~~~~~~~~~~~~~~~~~~ ## ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~webshag贵用法示例
[email protected]:~# webshag-gui